The Untold Story - Anecdotes from the OpenSSL China tour
26 February 2018
Table of Contents
- Why this article is here?
- The Pick-up Adventure
- Do you have WeChat, Dude?
- What’s Your Feeling back in Alibaba
- The “Twins”
- Liger or Tigon?
- Damn, the Boarding Pass is Lost
- Did We Fuck up the OpenSource Event?
- Worm Dinner
- Drunk as a Lord
- The Final “Haul Ass”
Why this article is here?
As most people have already known that OpenSSL has been in China for several days in September, from 17th to 25th specifically. The stories describing the very formal activities we had experienced during those days, have been reported by some media articles after the tour, thus many people knew what we have done in China, in particular the business part. But from my perspective, there were also things which were not disclosed yet, but should be told. I consider them as ‘anecdotes’: something made this China tour much more vivid and enjoyable. And this is why I decided to write these words. I would like to record the moments and memories we had together back in those nine days in China.
Before I tell you the amazing and funny stories, I will thank again the following BaishanCloud staffs who put huge efforts into this tour (In order of appearance in the stories): Jane, Sean, Jedo, Paul (me, absolutely), Shirley, Alan. And also the people didn’t show them up in the stories: Jenna, Amy, Mr. Wei An, our CTO Mr. Jian Tong and my boss Terence and Mel :-). Thank you all very much for supporting our ‘operation’. I also would like to thank the guys from OpenSSL for your patience for suffering a lot from our poor oral English ;-).
The Pick-up Adventure
The pick-up at the airport for the guys of OpenSSL was more scared than hurt. The original plan was: “Jane and Sean went to Shanghai Pudong airport to pick up Matt in the morning and then Jane accompanied with Matt back to the hotel while Sean stayed at the airport waiting for Steve, who would arrive at noon. Meanwhile, Jedo would go to Shanghai Hongqiao airport to pick Richard”.
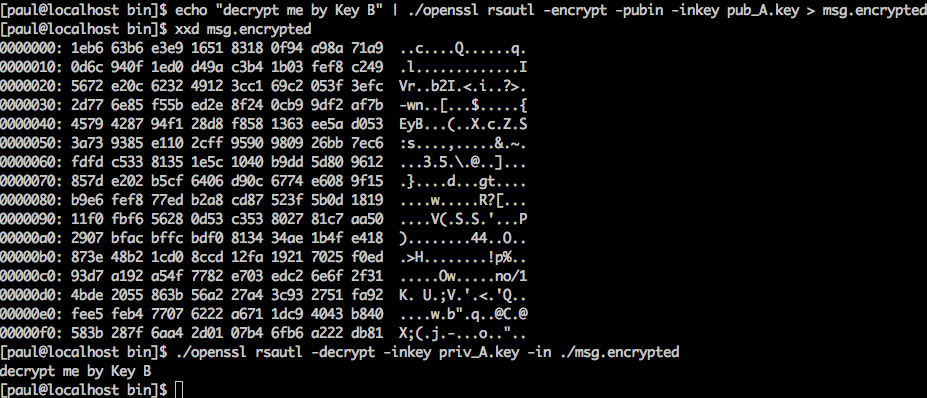
After Matt and Jane arrived at the hotel, we took this photo, and this was also the first photo in the China tour:

Lunch with Matt
Everthing ran smoothly until the afternoon. Sean called to tell me that Steve didn’t show up at the airport but the plane had already landed for almost 2 hours. We didn’t have any method to contace Steve since Steve bought himself a SIM card in US but that card didn’t work in his phone before he left his country. So we asked the airlinesm and they told us Steve didn’t board. That was very confused for us, so we contacted Beijing to check the filght information of Steve. Finally we found that someone in BaishanCloud made the flight wrong and the true time of arrival of Steve should be in the evening. So Sean had to continue to wait at the airport to pick up Steve. That was a though day for him anyway…
At last in the evening, around 7 o’clock, we picked up Steve, Tim and Rich. On the way back to the hotel, Rich teased me that I also needed to handle the problem with jetlag. And he was correct about this, since I usually slept at 3:00AM and woke up at 9:00 ~ 10:00AM in the same day, but during the tour I needed to adjust that life style.
Do you have WeChat, Dude?
When I met Matt, I gave him a Chinese local SIM card thus he could use the mobile network in China. We also prepared one SIM card for Richard, and both of the cards worked well with their cell phones. As mentioned before, Steve used a Chinese local SIM card bought by himself. Tim and Rich just used their own numbers ‘internationally’. So the result was, except Steve (he used a 2G network GSM phone), all other guys had 3G/4G access, it’s time to move to a more Chinese style communication.
I first helped Matt set up a WeChat account, and the next day all guys had their WeChat account, we even created a chat group there. Richard seemed to be interested of the WeChat app and played with the funny features for some time. That chat group helped a lot to coordinate schedules during the 8-day tour.
All guys kept using their WeChat even after they left China, for instance Tim and I chatted a lot by WeChat.
What’s Your Feeling back in Alibaba
On 18th September, we went to Alibaba HQ, the Xixi campus in Hangzhou. Rich and I have met here back in 2015, two days before that year’s Tmall double eleven festival. I resigned from Alibaba in June 2016, and this was the first time I came back here since then.

First met with Rich in 2015
After the meeting we took a walk in the campus, Rich asked me about what I felt coming back again here. Well, it’s a little complicated. I first worked on OpenSSL (as well as other SSL/TLS and cryptography stuffs) was in Alibaba, in 2014. The most important thing I’ve gotten in this company was the opportunities to widen my vision during last two years. That meant a lot to me. Back to the feelings, I was very happy to meet some old buddies there and was cherished the memory a little of those day-and-night when we fought together.

Sculpture in Alibaba
The “Twins”
After hanging out in Alibaba HQ, we departed for Shenzhen next day and it’s Shirley who picked us up at the airport and we planed to visit Tencent and Huawei.

Depart for Shenzhen
It’s very interested when we took a tour in Huawei’s exhibition center - a place showing the company’s most advantage techniques. One of the most interesting thing was there was a VR game section and two person could play it together to experience Huawei’s 5G tech. To play the VR game, a special device was needed and it would be convenient if the player didn’t wear glasses. Since Matt and Rich were the only two guys who didn’t wear glasses, so they went on the stage.

The “Twins”
This is funny and it reminded people of a 1988 movie with the name ‘Twins’. The game was about shooting zombies and it was very entertaining even just to watch the players shooting to the air for audience.
Liger or Tigon?
Having finished the visit to Huawei in the morning, we went to the zoo in the afternoon. This was a very educational trip that I learned two new English words - Liger and Tigon.

Richard was photographing
A Liger is the hybrid cross of a lion father and a tiger mother, apparently the word Liger itself indicates this already. To the contrary, a Tigon comes from a tiger father and a lion mother. I have seen them in the zoo in Shenzhen, but to be honest, I still can not distinguish them accurately as I always considered no matter which one is the father, the children should seem very similar but only the names are different. It could be interesting if I dig into this topic deeper in the future.
And we also had the chance to feed the big cats in a well ‘armoured’ bus, that was excited.

The bus we were in
The driver drove the bus into the ‘free-ranging’ area. Everyone in the bus had a fork and a piece of chicken leg - which was used to feed the tigon/liger/tigers.

The portal to the wild, Jurassic Park?
Actually it was a little tricky to feed the big cats - the best method was to ‘seduce’ the big cats with the chicken and didn’t put it too close to them, thus the big cats would cling to the safety nets of the bus and people inside could have more time to watch them.

I think this should be a Tigon
If you put the chicken too close to them, they would have the chicken and kept far from the bus - but in practice, it was hard to achieve this so we ran out of chicken quickly.

This is a real tiger
Damn, the Boarding Pass is Lost
On 21 September, we left Shenzhen and headed to Beijing. An adventure happened in the airport - I lost my boarding pass just before the boarding gate was closed.

Moment that I still had my boarding pass
I went to the boarding gate to ask if I could use the ID card for boarding, the answer was negative and I had to go to the counter of Shenzhen Airlines to reprint the boarding pass - the counter located several hundreds meters away from the gate and it was only 15 minutes before the gate got closed.
Sean and I rushed madly back to the counter of the airlines and meanwhile Rich and Jedo stayed at the boarding gate trying their best to prevent the gate from closing. I have not run at that pace for a decade I guess. Eventually we made it and boarded into the plane.
It felt good to see the night of Beijing with all other guys! It was more scared than hurt anyway!

Arrival in Beijing
Postscript: Several days later when I got home and cleared up my backpack, I found the ‘lost’ boarding pass at the bottom of my backpack. Damn it, I should be more careful.
Did We Fuck up the OpenSource Event?
In Beijing we had lots of work. And the most important agenda would be the open source event on 23 September. Everyone was going to give a speech in that afternoon.

Meeting in BaishanCloud office
We actually didn’t know what we prepared interested the audience or not. And we didn’t know if the simultaneous interpretation service in the saloon was good or not. It was not easy for the audience to have a most-English open source event.

Preparing
Everyone didn’t know if we would mess up the presentations or not. If no one likes to ask questions or doesn’t understand the speech well, that would a catastrophe. Lots of media persons awaited for writing report there, I hoped the atmosphere could be ‘hot’.

Matt’s talking about TLS13
After I have done my presentation, Steve, Tim and I were grabbed to another room to have an interview so I didn’t really aware of how it was going outside there. And I missed all the presentations after mine, which should be Rich, Richard and Tim. Some topics in their slides were also interest me a lot, but no chance to listen the speech lively.
The result was excellent by the feedback from staffs of BaishanCloud.

Group photo with some audience
According to Tim, they were asked questions after the event was over. And many Chinese technical guys were very interested in TLS 1.3, Post-Quantum Cryptography and also other topics we have talked about.
This was the first time BaishanCloud held such an event and it was also the first time OpenSSL presented in China. It was not easy, but we conquered it. We have done a great job and the what left was just to have a relax time in China!
Worm Dinner
Our CTO Mr. Jian Tong, on behalf of BaishanCloud, held a small banquet for our guests in the evening of 23 September. The dinner was in a very decent Spanish restaurant and I was lucky again that night…
I ordered fish, fried if I recall correctly. Along with the fish, there was salad in the dish. After I have eaten half of the fish, I found something wriggling in the dish, the light was poor so I didn’t see it clearly at first. And then that thing kept moving. I took a close look and I found it was like a ‘thread’ there, alive. I was panic. Then I called the waiter and they were panic.
Very quickly, the manager, a foreigner I couldn’t figure out his nationality, came to me and apologized very sincerely for the disaster, in English. I was curious that why he didn’t talk in Chinese since Tim heard he talked in Chinese to the waiters. But anyway, I pardoned this tragedy because I was in very good mood that night. After all we have done a tough job in the afternoon.
Finally they supplied new food for me, for free of course. By the way, the wine was good in that restaurant ignoring the ‘worm’ ;-)
We took a walk in the shops nearby after finishing the dinner, waiting for the bus to pick us up back to the hotel. Guys were happy and played around.

Rich with cool glasses
Drunk as a Lord
Tim, Rich and I went to a bar at night to celebrate. We drank several ‘cannon’s beer that night. For me, I might need some alcohol to reduce the effect of ‘worm’.
We have talked a lot of interesting stuffs such as the culture difference, the history of OpenSSL project, the Tao of open source etc. Some friends of mine joined the party and thus it’s more diverse to understand different Chinese attitudes toward open source.
We got back at around 4 AM in the morning and I went to bed in my boots, literally. And I woke up at around 6, because we have schedule to take a tour in Beijing.
When I was in the bus, I was something like this:

Photographed by Tim. Good capture!
The Final ‘Haul Ass’
The last part was the touring in several places in Beijing city, including the Forbidden City and Shichahai. This was described in Tim’s blog post on OpenSSL website, so I will skip this part in this article since here comes only the ‘untold’ parts.
The phrase ‘Haul Ass’ and its synonyms were frequently used by me during the whole journey when I needed to call for a move. I didn’t notice it had comedy effect at first, but it seemed so.
Tim was the first person who departed, on 24 September. And then the other guys on 25th. I made my final ‘Haul Ass’ at the airport to bid them farewell.
Rich, on behalf of OpenSSL, has sent me a party hat after he got back to USA and I like that very much, thanks!

Party hat with two beer slots
It was not a long trip in China, but as I mentioned earlier, this was the first time members of OpenSSL were here, so it’s important. I hope this trip was a start to make a channel of communication between China and the international open source community, which can help more Chinese developers to understand how to participate in the community. The community can also benefit from intelligence in China, to help the software being more widely used in Chinese market.
All things are difficult before they are easy. And the first step is always the hardest. But fortunately, we get this done and I am optimistic about the future.
Hope to meet you guys again!